介绍

之前我们看了如何利用nginx进行端口转发,其实更轻量的haproxy也许更合适。
原因很简单,纯粹,效率高,支持udp,简单。
介绍一下HAProxy:
简单的来说 HAProxy 就是一个负载均衡,TCP 和 HTTP 的代理程序,开源,高可用,C 写成。他原本的作用是将前端的大量流量分发到后端的服务器中,用于负载特别大的 WEB 网站的,这里被大材小用了。
使用 HAProxy 中转 SS 流量至少需要两台 VPS,国内一台,国外一台,SS 客户端直接连国内的 VPS,而通过国内的 VPS 转发流量到国外的 VPS 上。
安装
Debian/Ubuntu: sudo apt install -y haproxy Centos: sudo yum install -y haproxy
配置文件位置:/etc/haproxy/haproxy.cfg,我们只需要修改配置文件即可。
转发
这里我们只示范转发到域名的方式,分为tls模式和非tls模式。
非tls模式
监听本地49999端口,转发到test1.vpsxb.net的80端口
global
ulimit-n 51200
log /dev/log local0
log /dev/log local1 notice
chroot /var/lib/haproxy
pidfile /var/run/haproxy.pid
user haproxy
group haproxy
daemon
maxconn 20480
maxconnrate 20480
maxsslconn 20480
spread-checks 0
defaults
log global
mode tcp
option http-server-close
option dontlognull
timeout connect 5000
timeout client 120000
timeout server 120000
frontend frontend_49999_frontend
bind *:49999
bind :::49999 v6only
mode tcp
tcp-request inspect-delay 2s
tcp-request content accept if { req.ssl_hello_type 1 }
acl is_test1.vpsxb.net hdr_dom(host) -i -n test1.vpsxb.net
use_backend backend_49999_backend_test1.vpsxb.net if is_test1.vpsxb.net
backend backend_49999_backend_test1.vpsxb.net
mode tcp
server backend_49999_backend_test1.vpsxb.net_server test1.vpsxb.net:80 cookie test1.vpsxb.net_server
tls模式
监听本地49999端口,转发到test1.vpsxb.net的443端口
global
ulimit-n 51200
log /dev/log local0
log /dev/log local1 notice
chroot /var/lib/haproxy
pidfile /var/run/haproxy.pid
user haproxy
group haproxy
daemon
maxconn 20480
maxconnrate 20480
maxsslconn 20480
spread-checks 0
defaults
log global
mode tcp
option http-server-close
option dontlognull
timeout connect 5000
timeout client 120000
timeout server 120000
frontend frontend_49999_frontend
bind *:49999
bind :::49999 v6only
mode tcp
tcp-request inspect-delay 2s
tcp-request content accept if { req.ssl_hello_type 1 }
acl is_test1.vpsxb.net req_ssl_sni -i -n test1.vpsxb.net
use_backend backend_49999_backend_test1.vpsxb.net if is_test1.vpsxb.net
backend backend_49999_backend_test1.vpsxb.net
mode tcp
server backend_49999_backend_test1.vpsxb.net_server test1.vpsxb.net:443 cookie test1.vpsxb.net_server
端口复用
非tls模式
监听本地49999端口,转发到test1.vpsxb.net和test2.vpsxb.net的80端口:
global
ulimit-n 51200
log /dev/log local0
log /dev/log local1 notice
chroot /var/lib/haproxy
pidfile /var/run/haproxy.pid
user haproxy
group haproxy
daemon
maxconn 20480
maxconnrate 20480
maxsslconn 20480
spread-checks 0
defaults
log global
mode tcp
option http-server-close
option dontlognull
timeout connect 5000
timeout client 120000
timeout server 120000
frontend frontend_49999_frontend
bind *:49999
bind :::49999 v6only
mode tcp
tcp-request inspect-delay 2s
tcp-request content accept if { req.ssl_hello_type 1 }
acl is_test1.vpsxb.net hdr_dom(host) -i -n test1.vpsxb.net
acl is_test2.vpsxb.net hdr_dom(host) -i -n test2.vpsxb.net
use_backend backend_49999_backend_test1.vpsxb.net if is_test1.vpsxb.net
use_backend backend_49999_backend_test2.vpsxb.net if is_test2.vpsxb.net
backend backend_49999_backend_test1.vpsxb.net
mode tcp
server backend_49999_backend_test1.vpsxb.net_server test1.vpsxb.net:80 cookie test1.vpsxb.net_server
backend backend_49999_backend_test2.vpsxb.net
mode tcp
server backend_49999_backend_test2.vpsxb.net_server test2.vpsxb.net:80 cookie test2.vpsxb.net_server
tls模式
监听本地49999端口,转发到test1.vpsxb.net和test2.vpsxb.net的443端口:
global
ulimit-n 51200
log /dev/log local0
log /dev/log local1 notice
chroot /var/lib/haproxy
pidfile /var/run/haproxy.pid
user haproxy
group haproxy
daemon
maxconn 20480
maxconnrate 20480
maxsslconn 20480
spread-checks 0
defaults
log global
mode tcp
option http-server-close
option dontlognull
timeout connect 5000
timeout client 120000
timeout server 120000
frontend frontend_49999_frontend
bind *:49999
bind :::49999 v6only
mode tcp
tcp-request inspect-delay 2s
tcp-request content accept if { req.ssl_hello_type 1 }
acl is_test1.vpsxb.net req_ssl_sni -i -n test1.vpsxb.net
acl is_test2.vpsxb.net req_ssl_sni -i -n test2.vpsxb.net
use_backend backend_49999_backend_test1.vpsxb.net if is_test1.vpsxb.net
use_backend backend_49999_backend_test2.vpsxb.net if is_test2.vpsxb.net
backend backend_49999_backend_test1.vpsxb.net
mode tcp
server backend_49999_backend_test1.vpsxb.net_server test1.vpsxb.net:443 cookie test1.vpsxb.net_server
backend backend_49999_backend_test2.vpsxb.net
mode tcp
server backend_49999_backend_test2.vpsxb.net_server test2.vpsxb.net:443 cookie test2.vpsxb.net_server
tls与非tls混用:
监听本地49999端口,转发到test1.vpsxb.net的80端口和test2.vpsxb.net的443端口:
global
ulimit-n 51200
log /dev/log local0
log /dev/log local1 notice
chroot /var/lib/haproxy
pidfile /var/run/haproxy.pid
user haproxy
group haproxy
daemon
maxconn 20480
maxconnrate 20480
maxsslconn 20480
spread-checks 0
defaults
log global
mode tcp
option http-server-close
option dontlognull
timeout connect 5000
timeout client 120000
timeout server 120000
frontend frontend_49999_frontend
bind *:49999
bind :::49999 v6only
mode tcp
tcp-request inspect-delay 2s
tcp-request content accept if { req.ssl_hello_type 1 }
acl is_test1.vpsxb.net hdr_dom(host) -i -n test1.vpsxb.net
acl is_test2.vpsxb.net req_ssl_sni -i -n test2.vpsxb.net
use_backend backend_49999_backend_test1.vpsxb.net if is_test1.vpsxb.net
use_backend backend_49999_backend_test2.vpsxb.net if is_test2.vpsxb.net
backend backend_49999_backend_test1.vpsxb.net
mode tcp
server backend_49999_backend_test1.vpsxb.net_server test1.vpsxb.net:80 cookie test1.vpsxb.net_server
backend backend_49999_backend_test2.vpsxb.net
mode tcp
server backend_49999_backend_test2.vpsxb.net_server test2.vpsxb.net:443 cookie test2.vpsxb.net_server
重启haproxy
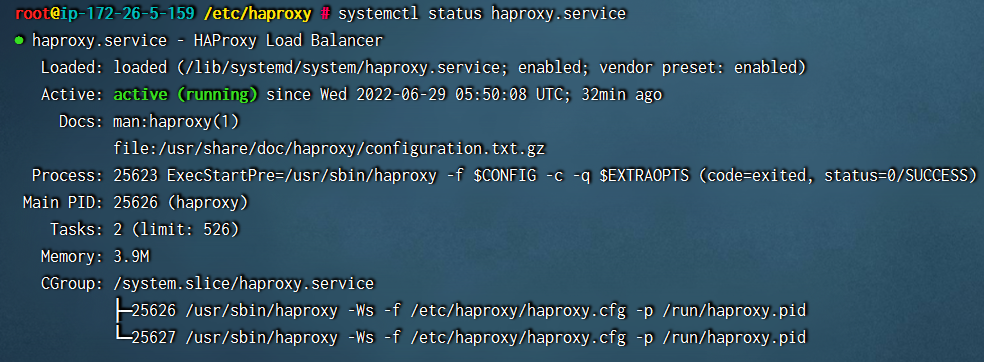
systemctl restart haproxy.service
我们查看下haproxy状态,已经正常运行: